In the ever-evolving landscape of cyber threats, traditional security models have hit their limits....
How Microsoft 365 Defender is changing the threat detection game
Over 25 years ago in the ’90s, my IT career started with antivirus vendors and technology like McAfee and Norton which came on floppy disks. In that time, I have seen a lot of antivirus vendors and technology have their day in the sun. Although there were some key milestones like enterprise management, antivirus got stuck as a reactive last line of defence for a long time. Antivirus was always caught on the back foot having to wait for malicious applications such as viruses and malware to be identified before their file hashes or patterns could be added to definition lists and thus detect and hopefully remove them.
Now in 2022, it is fair to say that we have come a long way. No longer do we talk about these products as just antivirus, they are now included as part of our proactive security solutions which I believe is due to a radical shift away from pattern-based detection. Malicious applications are no longer just detected by what they are, but by how they behave.
This shift towards behavioural-based detection has put security vendors on the front foot, enabling antivirus applications and services to stop potentially malicious code from running based on what it was trying to do, even if the code had not been seen before. This was the beginning of EDR (Endpoint Detection, and Response), it was not called that back then, but the cloud was not called the cloud when it first started either!
Think about it, the fundamental principle of modern EDR and XDR (Extended Detection and Response) solutions is to assume that a breach has already occurred and that you just have to find it. This is what behavioural detection was designed to do, assume nothing and try to verify everything.
There have been some stand-out EDR security products over the last few years like Panda, SentinelOne and Crowdstrike which have paired really well with the Microsoft Windows platform, but as good as they are, they are limited to the signals they get from the local operating system that these products are trying to protect. This is where Microsoft has differentiated itself with its new XDR Defender security product.
Microsoft has aligned their security products into a cohesive bundle under its Defender product brand.
- Defender for endpoint
- Defender for Office365
- Defender for cloud apps
- Defender for Identity
- Defender for Azure
- Defender EASM (External attack surface management)
What makes Defender special is not just this product alignment but the fact that it does go more than skin deep. These services share signals that on their own wouldn’t be significant, but collated together and analysed they offer powerful insights into cleverly orchestrated threats that could otherwise slip through. Defender is the next evolution of XDR threat protection and it's available for every Microsoft 365 tenant.
Now, I will concede that there is a level of commitment to the Microsoft 365 licensing that some organisations will be uneasy about, an upgrade from Business Premium or E3 to an E5 is not to be taken lightly. However, there are many ways to skin a cat and the Microsoft licensing SKUs are no different. If E5 is out of your reach then using add-on SKUs for “Defender for endpoint” and “Defender for Office 365” is a great start. I believe that when an organisation balances the cost of paying for obsolete security products, the increase in investment is a serious consideration.
The new Microsoft 365 security portal can provide an in-depth summary of your security posture and provide you with real-world suggestions and proactive tasks that you can take to further reduce vulnerabilities. Below is an example of this dashboard:
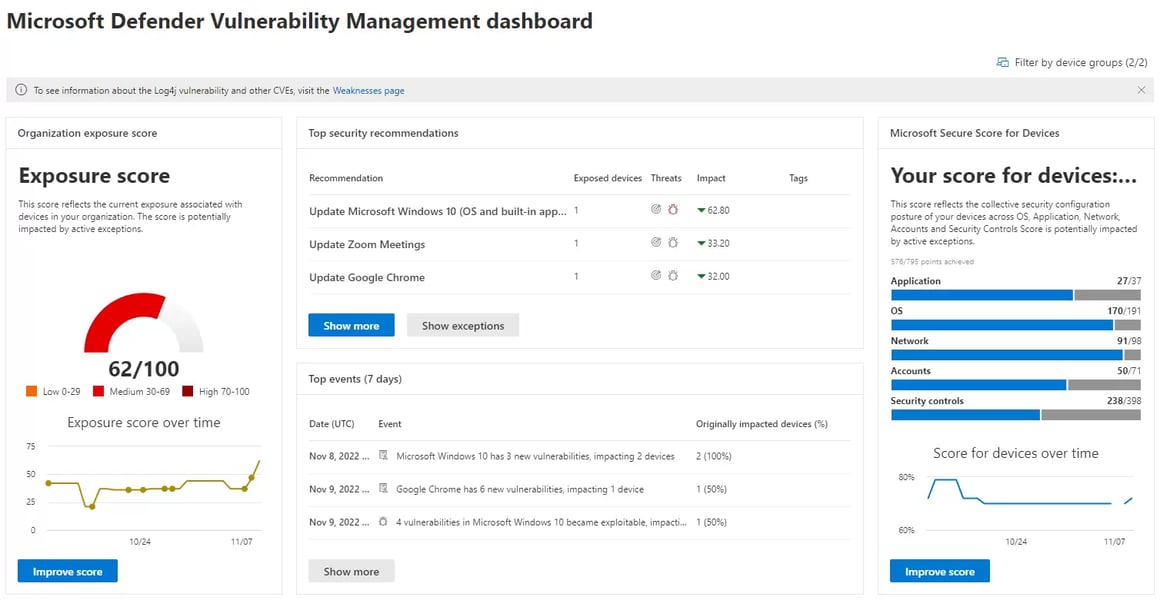
MS Defender Vulnerability Management Dashboard
Within the new dashboards, there are useful scoring metrics and task assignment capabilities that help stay focused on what you can do to make the best impact on your organisation's security posture. Here are my five favourites in Microsoft’s new 365 security portal.
Microsoft Secure Score
This is the first place to start and is an amazing tool to help you get an understanding of your Microsoft 365 tenant's security posture. It is full of recommendations on what you can do for your organisation and has links to all the information you need, check out the Microsoft Learn article here.
Microsoft Defender Vulnerability Management Dashboard
If you want to know how exposed you are to the current known vulnerabilities and what you can do about it then this is the place for you. This will make you feel like you have a 24/7 SOC working just for you, here you can prioritise tasks based on what threats pose the most risk to your organisation, check out the Microsoft Learn article here.
Microsoft 365 Defender Incidents
Incidents are where the XDR capabilities really start to shine. This is where you will find an aggregation of defender indicators about Users, devices and resources like email. This helps paint a clear picture of an attack and gives you a head start in assessing your response. Check out the Microsoft Learn article here.
Attack Simulation Training
Practice makes perfect, and the attack simulation training is what you use to identify the staff that need a little more attention. This tool can be really fun to use and offers a wide range of simulations. Security is everyone's responsibility and these simulations are a great way to demonstrate that everyone needs practice. Check out the Microsoft Learn article here.
Device Timeline
Device timelines are a seriously underutilised feature of Defender for Endpoint. It gives you clear evidence of not just what an attacker has tried to do but what was happening before and after the attack. You can search and sort events easily, simply being able to observe a file download or a USB key activating tells a compelling story and removes the guesswork. Check out the Microsoft Learn article here.
There is so much to love about what Microsoft has put together here, and the crowning achievement is you don’t have to be an Infosec geek to understand and use it with confidence.




