DDoS attacks can be a somewhat confusing subject. On one hand, volumetric attacks have been around for a long time with a number of solutions. On the other hand, the devil is in the detail with how effective solutions may be.
Here are some tips on understanding and reducing the risk of DDoS attacks or mitigating them.
Firstly, what is a DDoS attack?
A Distributed Denial of Service (DDoS) attack is a fairly crude attack that is designed to overwhelm the target with a volume of traffic. It is similar to being on poor broadband and having everyone in the house trying to watch Netflix at the same time. There simply isn't enough capacity to serve all parties. The Distributed part of a DDoS means that the traffic comes from a number of different "attackers", rather than just one or two in a DoS attack.
Launching a DDoS attack can be as simple as signing up online and paying some Bitcoin, then entering your target.
This makes it harder to block as you can't simply identify a couple of sources. So who are the "attackers"? I put it in quotes for good reason - often the sources in a DDoS attack aren't actually attackers, they are often made up of compromised devices with the owners having no idea. In layman's terms, if you have a Windows 7 PC attached to the Internet and haven't stayed current with updates, it could get a virus. Rather than corrupting your computer, that virus could instead allow your computer to be used to generate traffic as part of a DDoS attack. Equally a smart device in your home with a vulnerability could be used in a similar fashion... yes they can even weaponize your fridge!
The target of a DDoS attack is a DNS name (www.yourbusinessname.com) or an IP address which is like a street address for your network or website.
So how can you defend against DDoS attacks?
Reduce your attack surface and turn your data centres dark to the Internet
In English, please? What this really means is that you should look to reduce exposing your digital footprint directly to the Internet which is where DDoS attacks originate. If someone wants to attack your businesses, first they need to identify what they can attack. There are a few typical ways to do this:
- By finding your business's digital footprint online. The IP address for digital assets like your website, or your customer portal is easily looked up (that's a good thing) allowing attackers to target them (which is bad!).
- By sending phishing emails to your employees. When your employees click links in phishing emails or enter their work email address on untrustworthy websites, it allows attackers to associate your business with the IP your employee came from. This way they can learn your office IP address.
- By running a port scan. A port scan cycles through IP addresses and tries to connect to them to see if there is any response. If it gets a response it will record the response and the type of response it received. This can identify services on your network that are not published publicly (unlike your website) but could be targeted for an attack. For example, it may discover the IP address your employees use to connect to your VPN.
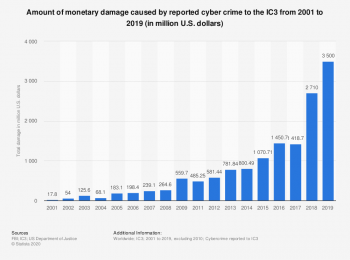
Less than 50% of the damage caused by Cybercrime is thought to be reported.
All these methods could be used to identify the target of a sustained and calculated DDoS attack. In a lot of instances, DDoS attacks are launched just to be a nuisance and therefore may not be targeted in a sophisticated means.
So how do you prevent your digital footprint being discovered? One answer is to cloak your services behind a cloud security service which means they are not directly exposed to the Internet. Here are some examples that relate to each of the points above. I will focus on cloud-based solutions as they are highly scalable and simple to deploy, making them a good starting point for most businesses.
- To prevent your own web server being attacked you can publish it to the Internet through a cloud WAF (web application firewall) service that includes a CDN (content distribution network) and DDoS protection service. Cloudflare and Akamai are examples of cloud WAF services This means when someone tries to connect to your web server they are instead connecting to the cloud WAF. The cloud WAF is designed to distribute the load of these connections globally so a single point doesn't get overwhelmed (CDN). It can also detect if there is a lot of load or abnormal traffic coming from particular sources and then block these or use another technique like rate limiting them. It does this before passing the legitimate traffic onto your web server, which should be configured to only accept connections from the WAF. Very simply this is like adding 1000 times more capacity to your web server.
- To prevent your office network being easily discoverable, you can use a cloud web security solution like Zscaler Internet Access. Unlike DNS based web security services, with Zscaler all your employee's Internet traffic would go via their cloud platform, which then proxies the traffic (i.e. acts as a proxy for your employee accessing the website they are browsing too) therefore hiding the origin of their location. This would mean if they clicked on a phishing link (assuming Zscaler didn't block it) or if they got malware on their machine, the malicious site they connected to would see Zscaler as an origin, not your network. If they then wanted to attack your network, they would instead attack Zscalers cloud platform, which is a massively scalable cloud platform designed to mitigate such attacks.
- To remove other network services from being targeted, you can take a similar approach and hide them behind a cloud security service. Two common items that businesses often have exposing their network are Citrix gateway and VPN concentrators. These allow users to dial in and access business applications over the Internet when they aren't on the corporate network. This also gives attackers something to target. Using a cloud platform like Zscaler Private Access to replace these, means that you no longer need to expose an endpoint on the public Internet for users remote access and therefore further reduces your attack surface.
Also if you use a public cloud provider for your IT systems, you will receive a level of inbuilt DDoS protection. AWS Shield Standard and Microsoft Azure DDoS Protection Basic are examples of this and can be used with other cloud services to mitigate DDoS attacks. You can also subscribe to more advanced DDoS protection services from cloud providers.
Using these methods in combination is the best approach. They are all complementary and all help reduce the number of targets for attackers.
DDoS mitigation services
Of course, nothing is foolproof and there are use cases where the above options may not work. This is where having a DDoS mitigation service from your Internet provider can be incredibly useful... but the devil is in the detail. You can pay a lot of money for a service that won't actually work.
Now here is where you need to scratch the surface a bit. Not all DDoS mitigation services are created equally.
To go even further, here is a warning, a number of ISPs trade on their brand or size to convince you that they offer the best solution. This is often not the case, and in fact, can be quite the opposite. Because they trade on reputation, not merit, they may actually offer a lesser service to a more specialised provider.
Remember DDoS attacks work by overwhelming the resources of the attack target. For example a web server. DDoS mitigation services work by removing or limiting abnormal traffic. So here are the things you need to consider when looking for a service provider
- Ask how much DDoS mitigation capacity your ISP is licensed for, and how large their upstream connections are. You need to ensure that your ISP has sufficient resources that they are not overwhelmed themselves. DDoS mitigation is expensive. Some of them will have limited licensed capacity which may not be enough to protect in a large enough attack, or if multiple clients are attacked at the same time.
- Ask your ISP where their DDoS scrubbing technology is implemented and if it is in every offshore POP. How the services are architected is important. Having DDoS mitigation implemented in offshore points of presence for example in Sydney or LA, allows traffic to be scrubbed before it even reaches NZ where resources are typically more limited or more expensive.
- Ask your ISP if they are able to advertise illegitimate sources to their upstream ISPs or other clients of their DDoS scrubbing technology. The most effective DDoS mitigation blocks the attacks closest to the source (the attacking device) meaning it never reaches a point of bottleneck. DDoS mitigation services that are able to tell other ISPs to stop the traffic before it even reaches your ISP are the most effective.
- Ask your ISP what their policy is on blocking your IP address if you are under attack. When an ISP is at risk of being overcome by a DDoS attack, they will "black hole" the target of the attack. This tells the ISPs they connect to not to send traffic for the specified IP address to prevent their own infrastructure from being overwhelmed. If this is your IP address, it is the same as disconnecting you from the Internet. This can be a good test to determine if your ISP really has the capacity or capability they profess to.
How do the cloud providers do it?
The way cloud services like Cloudflare, Akamai and Zscaler work is through the use of something called IP anycast. While an IP address is usually a specific location that Internet traffic is routed to, IP anycast publishes the same address in multiple global locations and allows traffic to be routed to the closest location that IP address is advertised. A cloud provider may have around 150+ data centres around the world where they advertise the same address. This means under a DDoS attack, the attack goes to 150+ locations, each of which has a huge amount of network and processing resources. Therefore they are difficult targets to overwhelm. When you are looking for DDoS mitigation services, you are really looking for this sort of model to be replicated as much as possible, hence the questions above.
A final note
Of course, nothing is foolproof, and we are often only able to select the best solution we can afford (until after an outage, where that budget item from the last 3 years is miraculously approved). It's always a good idea to have a backup plan. Something simple like a basic and static version of your website hosted on a cloud platform and behind a CDN is far better than nothing in the case of an attack. It's also cheap. Similarly being prepared for users to work from home, not the office, can be a straightforward disaster recovery plan (plus pretty well tested these days).



